Building secure web applications is crucial because of the sensitive data that is often handled by web applications. In today's digital age, web applications are used for various purposes such as online banking, eCommerce, and communication, all of which involve sensitive information. If a web application is not secure, it can lead to serious consequences such as identity theft, financial loss, and reputation damage.
A security breach can have a severe impact on the reputation of a company. Customers are more likely to trust companies that take their security seriously.
Many industries have compliance requirements that must be met to protect customer data. Building secure web applications can help meet these requirements and avoid costly fines.
According to recent statistics, web application attacks are increasing at an alarming rate. The following are some statistics that highlight the importance of building secure web applications:
The cost of a data breach has hit a new peak, according to an IBM report with an average of USD 4.35 million in 2022, marking a 2.6% rise from the previous year's average of USD 4.24 million. This represents a 12.7% surge from the USD 3.86 million average costs reported in 2020.
By CDNetworks, there has been a 12.56% rise in web application attacks compared to last year, resulting in a daily average of 62.8875 million attacks. Additionally, malicious bot attacks have seen a surge of 2.27 times compared to the same period in 2021, with a total of 77.366 billion incidents recorded.
According to a survey by Ponemon Institute, the average cost of a single data breach in the United States is $8.19 million.
These statistics show that cyber-attacks on web applications are a serious threat that can have significant financial and reputational consequences. Building secure web applications is therefore essential to protect against these threats and ensure the safety of user data. In this blog post, you’ll find out how to secure web applications.
Want a web app that does more?
Let's build a solution that's smart, sleek, and powerful.
Alina
Client Manager

Understanding Threats and Risks
Web application security threats are vulnerabilities or weaknesses in web applications that attackers can exploit to gain unauthorized access, steal data, or cause damage to the application or the organization.
Common web application security threats
- Injection attacks: This occurs when an attacker injects malicious code into a web application by exploiting vulnerabilities in the application. SQL injection and cross-site scripting (XSS) are some examples of injection attacks.
- Cross-site scripting (XSS): This type of attack occurs when an attacker injects malicious code into a web page that is then executed by a victim's browser. The attacker can use this to steal the victim's data, such as login credentials.
- Cross-site request forgery (CSRF): In this attack, the attacker tricks the victim into performing an action on the web application that they didn't intend to, such as making a payment or changing their password.
- Broken authentication and session management: If a web application has poor authentication and session management, it can allow attackers to gain unauthorized access to user accounts and steal sensitive information.
Examples of web application attacks
In 2017, Equifax suffered a data breach that exposed sensitive personal information, such as social security numbers and birth dates, of millions of its customers. The breach was caused by a vulnerability in the company's web application software.
In 2018, British Airways suffered a data breach that resulted in the theft of the personal and financial data of over 380,000 customers. The attackers were able to exploit a vulnerability in the company's web application payment system.
Potential impact of attacks on a business
- The potential impact of these attacks on a business can be severe and long-lasting. The consequences may include the following: Data breaches and other web application attacks can result in significant financial losses due to lost revenue, lawsuits, and fines.
- A successful web application attack can damage a company's reputation and erode customer trust, leading to loss of business and decreased revenue.
- Businesses that suffer data breaches may face legal liabilities if they fail to protect their customers' personal and financial information.
- Businesses that handle sensitive customer information are subject to regulatory requirements, and a data breach or other web application attack can result in non-compliance and penalties.
Best Practices on How to Secure Web Applications
Building secure web applications is crucial to protect user's sensitive information, prevent unauthorized access, and maintain the integrity of the system.
How to secure web applications with best coding practices and design principles
- Input validation: Ensure that all input received from users, including form fields and URL parameters, is validated and sanitized to prevent attacks such as SQL injection, cross-site scripting (XSS), and command injection.
- Authentication and authorization: Implement robust authentication mechanisms, such as multi-factor authentication, and ensure that users can access only the data and functionality they need.
- Secure communications: Use HTTPS and SSL/TLS protocols to encrypt data transmitted between the server and the client, preventing eavesdropping and data tampering.
- Data encryption: Sensitive data, such as passwords and credit card information, should be encrypted using strong encryption algorithms to prevent unauthorized access.
- Error handling and logging: Implement proper error handling and logging mechanisms to identify security vulnerabilities and respond appropriately to security incidents.
- Regular security updates of web application: Keep the web app and its underlying components up-to-date with the latest security patches and updates to address known vulnerabilities.
- Least privilege: Ensure that users and processes are granted only the minimum necessary rights to perform their tasks, reducing the risk of privilege escalation attacks.
- Defense in depth: Implement multiple layers of security controls, such as firewalls, intrusion detection systems, and anti-virus software, to reduce the risk of a single point of failure.
Overview of the cyber security frameworks available for web apps
There are several web application security frameworks, which provide guidelines and best practices to build secure web applications. Here are some of the most popular cybersecurity frameworks for web applications:
- ISO 27001: ISO 27001 is a set of international standards that provides guidelines for information security management systems. It covers all aspects of information security, including risk management, security policies, procedures, and controls.
- NIST Cybersecurity Framework: The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a framework for managing and reducing cybersecurity risk. It includes a set of guidelines, best practices, and standards that organizations can use to build a comprehensive cybersecurity program.
- PCI DSS (Payment Card Industry Data Security Standard): PCI DSS is a set of standards that applies to organizations that process credit card transactions. It provides guidelines and requirements for securing credit card data and preventing data breaches.
- CIS Controls: The Center for Internet Security (CIS) Controls is a set of guidelines and best practices that provides a prioritized approach to cybersecurity. The controls are designed to help organizations protect against the most common cyber attacks by implementing specific security measures.
- CSA Security, Trust & Assurance Registry (STAR): The Cloud Security Alliance (CSA) STAR is a registry that allows cloud service providers to demonstrate their security compliance and transparency to customers. The registry includes a self-assessment questionnaire that service providers can complete to demonstrate their security controls.
The importance of maintaining security throughout the development lifecycle
Maintaining security throughout the development lifecycle is crucial for ensuring that software and applications are secure and reliable, especially when protected by a non disclosure agreement for app development. Here are some reasons why:
- Early detection of vulnerabilities
- Cost-effectiveness
- Compliance requirements
- Protecting user data
- Maintaining trust
Users expect the software and applications they use to be secure, and incorporating security throughout the development lifecycle helps organizations demonstrate their commitment to security and maintain user trust. Overall, incorporating security into the development lifecycle is essential for ensuring that software and applications are secure and reliable, and it is much easier and cost-effective to address security issues early on in the process.
What are the Strategies to Secure Web Applications?
Web applications are essential to the modern business landscape, and securing them is critical to protect sensitive data and maintaining customer trust.
Overview of tools and techniques for securing web applications
Various tools and techniques can be utilized to secure web applications. The most commonly used ones:
- Web Application Firewalls (WAFs): A WAF is a security solution that is between the web application and the client, analyzing traffic to identify and block malicious requests.
- Vulnerability Scanners: These tools scan web applications for vulnerabilities, such as SQL injection or cross-site scripting, and identify potential areas of weakness.
- Penetration Testing: This involves simulating attacks on web applications to identify vulnerabilities and weaknesses in the application's security.
- Secure Coding Standards: Utilizing secure coding standards, such as the OWASP Top Ten, can help prevent common vulnerabilities from being introduced into the codebase.
- Encryption: Encrypting sensitive data, such as passwords or credit card information, with strong encryption algorithms can prevent unauthorized access to this information.
- Authentication and Access Control: Implementing strong authentication mechanisms, such as multi-factor authentication, and access control mechanisms, such as role-based access control, can prevent unauthorized access to the web application.
- Input Validation: Validating and sanitizing user input can prevent attacks such as SQL injection and cross-site scripting.
- Security Headers: Adding security headers, such as Content Security Policy and X-Frame-Options, can help prevent attacks such as clickjacking and cross-site scripting.
- Regular Patching: Applying patches and updates to the web application and its underlying components, such as web servers and operating systems, can address known vulnerabilities and ensure that the application remains secure.
The benefits of utilizing encryption, authentication, and access control mechanisms
The benefits of utilizing encryption, authentication, and access control mechanisms include:
- Protecting sensitive data: Encryption ensures that sensitive data is protected from unauthorized access, ensuring that customer information remains confidential.
- Preventing unauthorized access: Authentication mechanisms prevent unauthorized access, ensuring that only authorized personnel can access the web application.
- Control access: Access control mechanisms provide granular control over access to different parts of the application, ensuring that users only have access to the parts of the application they need.
Importance of ongoing monitoring and testing
Ongoing monitoring and testing are critical to maintaining the security of web applications. Regular testing can detect vulnerabilities before they are exploited by attackers, enabling timely remediation. Additionally, ongoing monitoring ensures that web applications are secure over time, as new vulnerabilities can emerge over time.
Securing web applications requires a multi-faceted approach, including secure coding practices, encryption, authentication, access control, and ongoing monitoring and testing. Organizations that implement these strategies can protect sensitive data, prevent unauthorized access, and maintain customer trust.
Our Experience
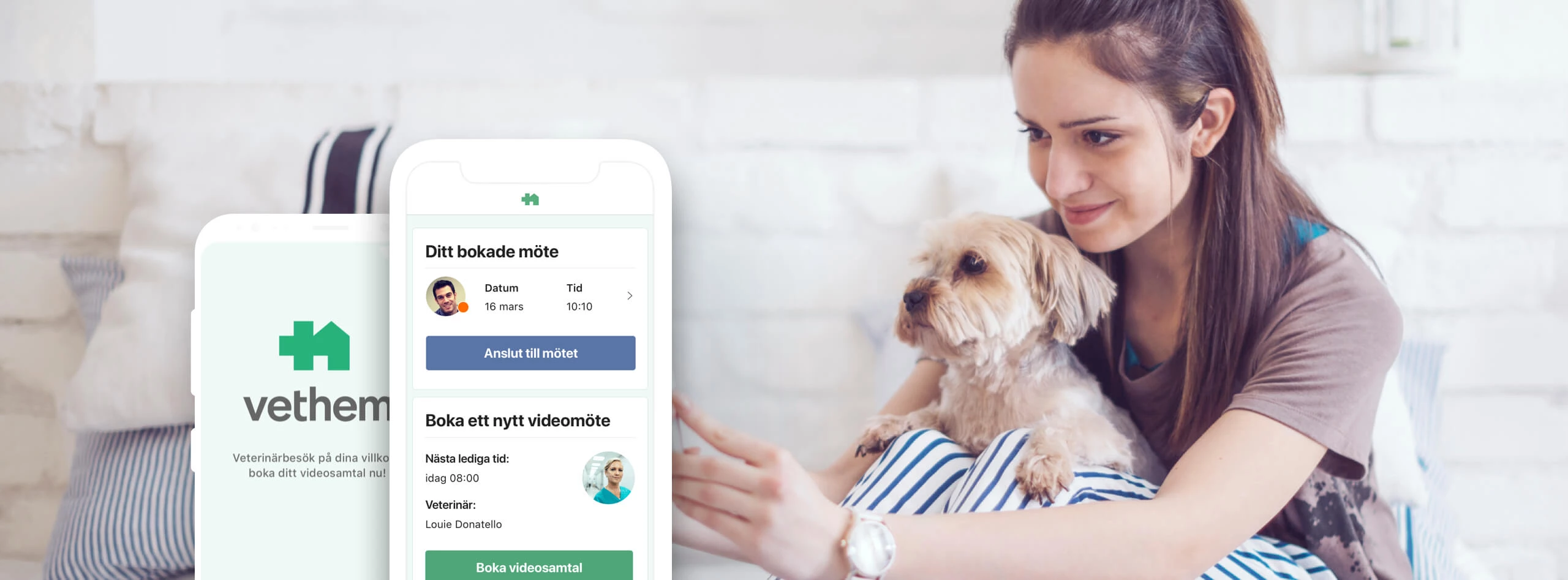
Vethem (now Agria)
When developing a Vethem - vet appointment booking app, we understood that users value secure, quick, and hassle-free site authorization. To provide the best experience for our users in Sweden, we’ve made the authorization process as simple as possible by implementing the BankID authorization option.
We also recognize that different regions may have different preferences for authorization methods, we offer customized authorization options tailored to our customer's specific needs, taking into account regional peculiarities and the user's convenience.
Emerging Threats and Potential Future of Web Application Security Challenges
- Artificial Intelligence (AI) and Machine Learning (ML) attacks: AI and ML attacks are expected to become more prevalent, as cybercriminals use these technologies to create more sophisticated attacks. These attacks can target vulnerabilities in web applications, bypass traditional security measures, and exploit user behavior patterns.
- Internet of Things (IoT) attacks: The increasing number of connected devices and their integration with web applications creates new attack surfaces. Attackers can use IoT devices to launch attacks against web applications, steal data, and compromise the security of the entire system.
- Quantum computing attacks: Quantum computing has the potential to break current encryption standards, making web applications vulnerable to attacks. While quantum computing is still in its infancy, it is expected to become more advanced in the coming years, creating a new threat landscape.
- 5G security challenges: With the rollout of 5G networks, web applications are expected to become more vulnerable to attacks due to increased speed and bandwidth. This can lead to a higher number of attacks, including DDoS attacks, ransomware attacks, and other types of cybercrime.
The future of web application security will require a holistic approach that incorporates innovative technologies, best practices, and a deep understanding of emerging threats and potential challenges. By adopting these approaches, organizations can ensure that their web applications are secure, resilient, and able to withstand the evolving threat landscape.
Bottom Line
Now you know what are the strategies to secure web applications. Building secure web applications is crucial because cyber-attacks and data breaches are rampant. It requires a combination of best practices, secure coding practices, and regular security assessments to protect your application against attacks.
Stfalcon is a software development company that specializes in web and mobile application development. We follow best practices for web application security, such as using HTTPS encryption, implementing access controls, and performing regular security audits.
Stfalcon's developers are trained in secure coding practices and can ensure that the code they write is free from common vulnerabilities, such as SQL injection and cross-site scripting (XSS) attacks.
Stfalcon performs thorough testing and quality assurance checks to ensure that clients’ web applications are secure and free from bugs and vulnerabilities.
Stfalcon, as a trusted web development services provider, knows how to secure web applications and can help ensure that web applications meet industry standards for security and compliance. If you are interested in cooperation, just contact us.

 Read the full case study
Read the full case study