
The General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act of 1996 (HIPAA) are pivotal data protection frameworks. GDPR, a comprehensive regime, broadly covers information about identified or identifiable individuals and applies to diverse organizations collecting and processing personal data within the EEA. On the other hand, HIPAA stands for a specific U.S.-based data protection framework and is limited to Protected Health Information (PHI) and certain designated healthcare entities.
Find comprehensive details on the HIPAA IT Compliance Checklist, offering guidelines you can explore in our blog post for in-depth insights.
Background of GDPR and HIPAA Regulations
Enacted by the EU in May 2016, the General Data Protection Regulation (GDPR) aimed to standardize data protection regulations across the EU, replacing the varied national laws within its Member States. Coming into force in May 2018 and subsequently integrated into the Agreement on the European Economic Area for EEA-wide applicability, the GDPR is comprehensive legislation applicable to entities involved in the collection or processing of personal data within the EEA. While it introduces stricter controls on handling health data and other sensitive personal information, the GDPR generally covers all types of personal data and organizations.
The genesis of the Health Insurance Portability and Accountability Act (HIPAA) dates back to a congressional statute in 1996. However, the statutory language itself lacked detailed privacy or security provisions. Congress entrusted the U.S. Department of Health and Human Services (HHS) with the task of formulating specific regulations for safeguarding health information. The HHS initiated this process in the early 2000s, resulting in the HIPAA Privacy Rule and HIPAA Security Rule. In 2009, the Health Information Technology for Economic and Clinical Health Act of 2009 (HITECH Act) amended HIPAA, leading to updated regulations and the introduction of the HIPAA Breach Notification Rule.
Comparing GDPR and HIPAA Regulations
In the United States, all medical facilities, healthcare practitioners, including doctors and nurses, and other designated "covered entities," along with individuals working directly or indirectly with these entities, commonly referred to as "business associates," are mandated to adhere to the Health Insurance Portability and Accountability Act (HIPAA) Security Rule for the management of protected health information (PHI). The primary objective of the Security Rule is to prevent breaches of patient data, and failure to comply can result in substantial fines. The HIPAA Security Rule necessitates healthcare service providers to implement the following safeguards within their organizations:
- Technical safeguards, incorporating healthcare software standards.
- Physical safeguards, addressing physical access to electronic PHI (ePHI).
- Administrative safeguards, encompassing organizational data protection measures.
Ensuring compliance is imperative, as violations may lead to significant penalties and damage a company's reputation. Notably, in 2020, Premera Blue Cross, a health insurance company based in Washington state, paid $6.8 million for the unauthorized disclosure of ePHI belonging to 10.4 million individuals.
Different countries have their legislation dedicated to ensuring the privacy of healthcare data. If you are considering entering markets with your healthcare software, this article on Comparing GDPR and HIPAA will be particularly relevant for you.
Want a web app that does more?
Let's build a solution that's smart, sleek, and powerful.
Alina
Client Manager

Individual Rights: Comparing GDPR and HIPPA
Both the GDPR and HIPAA confer various rights to individuals, presenting similarities in their provisions.
Right to be Informed:
- GDPR: Individuals have the right to receive detailed information about the collection and use of their personal data (Article 13 of the GDPR).
- HIPAA: are entitled to a Notice of Privacy Practices outlining Individuals how a covered entity uses and discloses their PHI. Additionally, they have the right to an accounting of disclosures upon request.
Right of Access:
- GDPR: Individuals can confirm whether their personal data is processed and have the right to access the stored personal data (Article 15 of the GDPR).
- HIPAA: Individuals possess the right to access their own PHI maintained by a covered entity.
Right to Rectification:
- GDPR: Individuals have the right to rectify or update their personal data for accuracy (Article 16 of the GDPR).
- HIPAA: Individuals can amend their PHI to ensure correctness.
Right to Restriction of Processing and Right to Object:
- GDPR: Individuals can restrict and object to the processing of their personal data (Article 18 of the GDPR).
- HIPAA: Individuals can request restrictions on certain uses and disclosures of their PHI, although covered entities may not be obligated to agree, except in specific circumstances.
Minimum Necessary:
- GDPR: Personal data processing must be adequate, relevant, and limited to what is necessary for the intended purposes (Article 5 of the GDPR).
- HIPAA: Covered entities and business associates must make reasonable efforts to limit requests, uses, and disclosures of PHI to the minimum necessary to achieve the intended purpose.
De-identification:
- GDPR: The GDPR allows for anonymization, rendering personal data anonymous to the point where the data subject is no longer identifiable. True anonymization is stringent and must meet high standards (Recital 26 of the GDPR).
- HIPAA: HIPAA permits the de-identification of PHI through the Safe Harbor Method or the Expert Determination Method. The Safe Harbor Method requires the removal of specific identifiers, and there should be no actual knowledge that the information could identify the individual. The Expert Determination Method involves applying accepted statistical and scientific principles to determine a minimal risk of identification by an anticipated recipient.
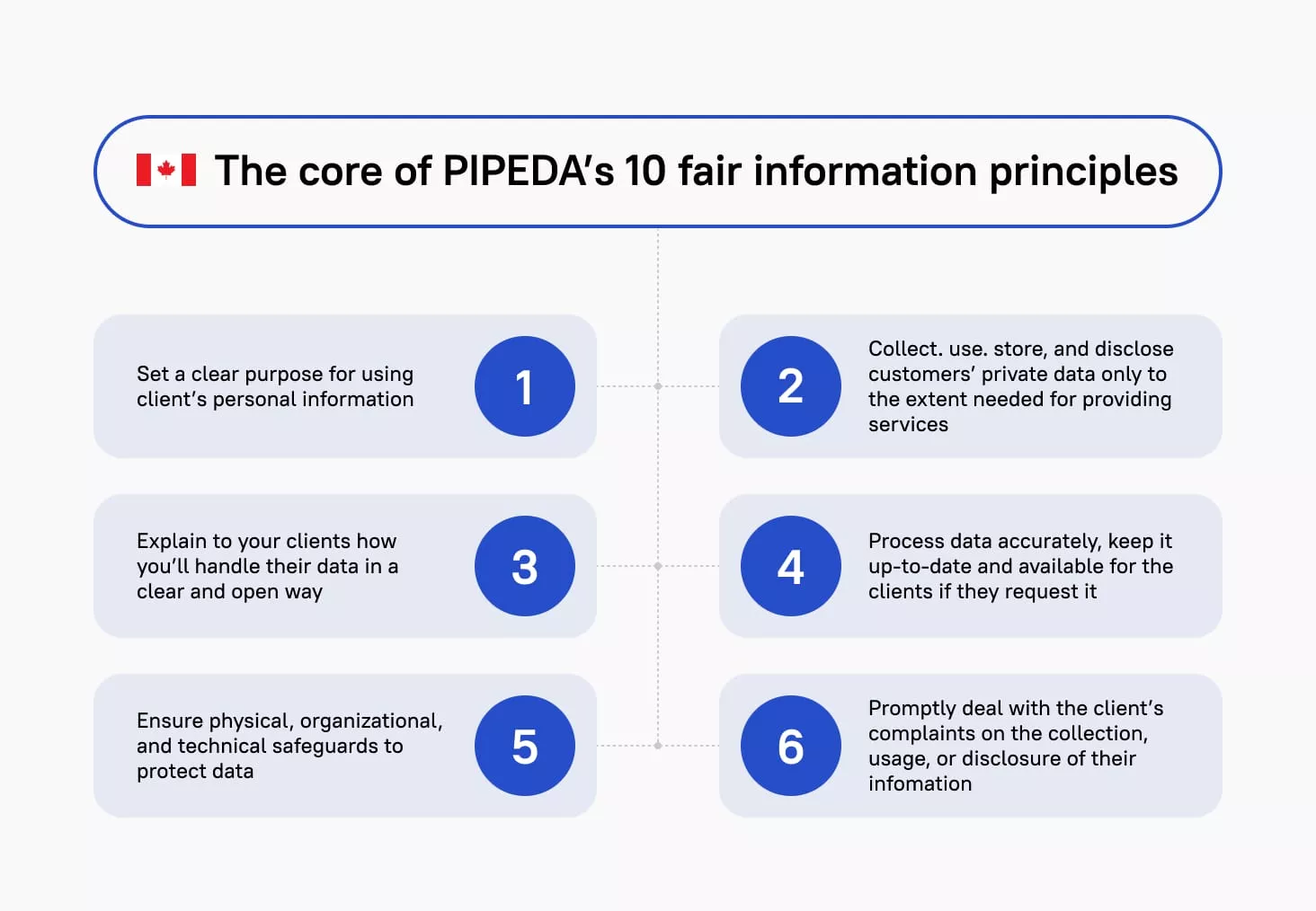
Comparing PHI Protections: PIPEDA in Canada vs. HIPAA in the United States
In Canada, the Personal Information Protection and Electronic Documents Act (PIPEDA) governs private sector entities involved in the collection, use, or disclosure of personal information for commercial purposes. This encompasses various entities, including physicians operating in private practices who receive direct payments from patients or reimbursement from provincial health plans or employment insurance plans.
PIPEDA extends beyond medical data to include personal information such as age, name, ID numbers, income level, ethnicity, credit records, loan records, and social status. Violations of PIPEDA can result in fines of up to CAD$100,000 (~US$82,500).
Outlined in the graphic below are the ten fair information principles at the core of PIPEDA.
Unlike the HIPAA privacy rule, which applies nationwide in the US, PIPEDA does not extend to the provinces of Quebec, British Columbia, and Alberta. For example, private businesses in Quebec must adhere to the Quebec Act Respecting the Protection of Personal Information in the Private Sector (the Privacy Act 1993). While its principles and penalties align closely with those of PIPEDA, the Quebec Privacy Act pertains to all private sector organizations, not just those engaged in commercial activities.
Before entering the Canadian business landscape, it's crucial to consider the specific privacy laws of the provinces in which your business operates. Ontario, for instance, has additional legislation called the Personal Health Information Protection Act (PHIPA), which exclusively covers PHI. Penalties for non-compliance with PHIPA can reach up to CAD$200,000 (~US$165,000) for individuals and up to CAD$1 million (~US$826,000) for healthcare organizations.
Similar to HIPAA, PHIPA regulates health information custodians (HICs) and PHI agents, with HICs akin to HIPAA's covered entities and PHI agents resembling HIPAA's business associates. While PHIPA shares similarities with HIPAA at its core, there are some distinctions. PHIPA offers a more generalized overview of data security safeguards, requiring healthcare custodians to take reasonable steps to protect data privacy without specifying these steps. Additionally, PHIPA mandates IT service providers to notify custodians of all privacy breaches and furnish, upon request, a record of all accesses and transfers of PHI associated with the custodian. Like HIPAA, PIPEDA, and other privacy laws in Canadian provinces, these regulations do not restrict organizations in the measures they implement to ensure the security of patients' data, as long as these measures lawfully and appropriately safeguard patients' data.
PHI requirements in the UK
In the United Kingdom, safeguarding health data entails a more intricate and rigorous process compared to the United States. Healthcare entities are obligated to adhere to numerous acts, undergo assessments, and conform to established standards. The UK government has curated an extensive array of comprehensive guides and policies to facilitate these procedures for healthcare enterprises.

The foundational legislation governing data privacy in the UK is the Data Protection Act 2018, encompassing overarching requirements for safeguarding personal information, including health data. Additionally, Protected Health Information (PHI) is subject to regulation under the UK General Data Protection Regulation (UK GDPR), where:
- Article 6 outlines the conditions that organizations must observe when handling sensitive data.
- Article 9 delineates instances wherein organizations are entitled to process sensitive data.
Within the UK, the National Health Service (NHS) not only oversees how organizations manage PHI but also regulates digital health products. Before entering the UK market, every healthcare software solution must:
- Be registered in the NHS Apps Library.
- Successfully undergo an NHS health app assessment.
- Conform to NHS digital, data, and technology standards.
Refer to the provided guide to good practice for digital and data-driven health technologies for insights on complying with these stipulations and ensuring a robust level of health data privacy.
HIPAA and European Tech Companies: Navigating Compliance
Although HIPAA is not explicitly designed to have extraterritorial reach, meaning it is not formulated for application outside the United States, its provisions safeguard the data of U.S. citizens globally. In legal terms, HIPAA de facto extends its jurisdiction beyond U.S. borders.
Given that HIPAA is crafted to protect the data of U.S. citizens, its applicability extends to any health tech company processing or storing medical data belonging to even a single U.S. citizen. Therefore, compliance with HIPAA becomes imperative under such circumstances.
HIPAA in Europe: Potential Fines for EU Health Techs
Determining precise figures for potential fines poses a challenge, with penalties ranging from $25,000 to $50,000 per individual record and escalating into multimillion-dollar fines. These fines may be imposed at both federal and U.S. state levels, adding complexity to the regulatory landscape. Additionally, the financial consequences overlook the significant reputational damage a health tech company may incur due to a HIPAA violation. For European companies aspiring to enter the U.S. market or secure U.S. investments, a HIPAA fine could jeopardize those prospects.
Compliance with HIPAA in Europe: Key Considerations
Compliance with HIPAA not only serves as a risk mitigation strategy for avoiding fines and negative publicity but also becomes a distinctive selling point. For health tech companies aiming to collaborate with U.S. counterparts or establish a presence in the U.S., adherence to HIPAA is essential. Achieving compliance opens doors to new market opportunities and potential business ventures with American companies.
Fortunately, aspects of GDPR compliance align with the requirements of HIPAA. Adjustments to privacy policies, consent-gathering processes, and, critically, data processing and storage methods are essential. Engaging in a compliance audit and collaborating to develop a roadmap for achieving compliance are proactive steps that health tech companies can take.
HIPAA in Europe is a regulatory framework that health techs must adhere to, not solely due to the risk of fines but primarily because interoperability and compliance unlock valuable opportunities for European companies in the U.S. market.
Our Experience
IsDocIn
The client provided detailed user stories, enabling us to promptly initiate work on the mobile interface prototype. Through consultations with the client, who possesses expertise in medical professional routines, and collaboration with their back-end team, we ensured a seamless experience for patients. Despite the challenge of adhering to procedures while creating a clear and user-friendly interface, we successfully developed an interactive prototype.
In iOS app development, we leveraged new features such as the UISearchController class for efficient data searches, UIAppearance class for streamlined parameter specification, and the Xcode tool "Refactor to Storyboard" for organized screen classification. Utilizing only standard libraries and elements in the iOS app minimizes potential issues associated with third-party solutions.
HospApp
We developed an Android application that encompasses key features for hospital staff. The Stfalcon team contributed to user interface design, Android development, manual testing, quality assurance, and implementation.
Our focus was on specific screens, including Messages, Chat room/group, and Tasks. The Messages section comprises a group list, where each group is associated with a patient and a specific category, such as cleaning, food, doctor, medical record, etc.
Conclusion
Many countries incorporate health data provisions within their overarching data privacy legislation, although not all explicitly outline specific measures for safeguarding this sensitive information. Certain countries, such as the UK, furnish comprehensive guidelines for interpreting data protection acts and offer recommendations on optimal compliance approaches.
Stfalcon's dedicated team possesses substantial expertise in developing comprehensive healthcare solutions. We are more than willing to support you in creating a secure healthcare product, just contact us.

 Read the full case study
Read the full case study
 Read the full case study
Read the full case study


